Los permisos de Android brindan controles que aumentan la conciencia del usuario y limitan el acceso de una aplicación a datos confidenciales. La configuración de permisos en Android 8.0 y versiones anteriores incluye listas de permitidos, sin las cuales las aplicaciones privilegiadas se deshabilitan, incluso si están en la ruta priv-app privada. En Android 9 y versiones posteriores, un dispositivo que intenta usar aplicaciones que no están en la lista de permitidos correctamente no se iniciará.
Android 10 introdujo el concepto de rol , un nombre único dentro del sistema asociado con ciertos requisitos y privilegios. Asigne roles a las aplicaciones para otorgarles permisos para un propósito específico y configure roles predeterminados utilizando los recursos de configuración de la plataforma.
Las mayores protecciones contra aplicaciones potencialmente dañinas (PHA) mejoran
- Transparencia en el comportamiento de las aplicaciones potencialmente dañinas.
- Control del usuario sobre el comportamiento de la aplicación.
- Discreción de los desarrolladores de aplicaciones al usar datos privados, protegidos por permisos.
Instalación y permiso del paquete
En Android 9 y versiones anteriores, las funcionalidades de instalación de paquetes y control de permisos estaban contenidas en el paquete PackageInstaller ( //packages/apps/PackageInstaller ). En Android 10 y versiones posteriores, la funcionalidad de control de permisos reside en un paquete separado, PermissionController ( //packages/apps/PermissionController ). La Figura 1 ilustra dónde residen los dos paquetes en Android 10.
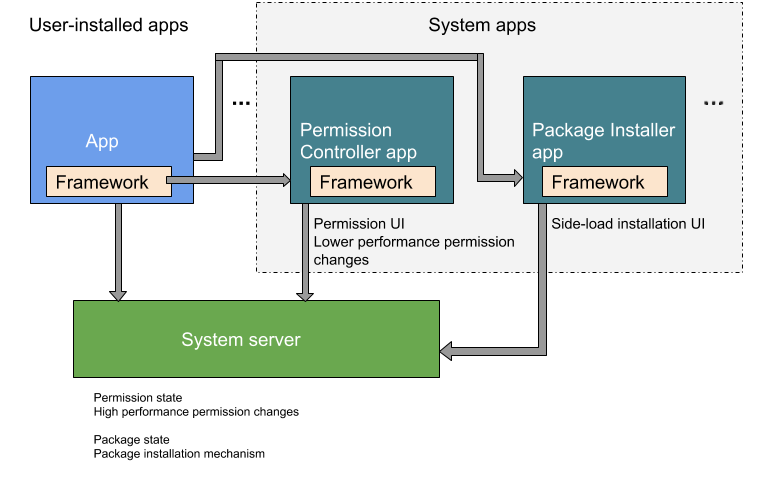
Listas de permitidos y acceso
En Android 6.0 y superior, las aplicaciones solicitan acceso a permisos peligrosos en tiempo de ejecución . Android 10 agrega permisos de tiempo de ejecución de reconocimiento de actividad (AR), que solicitan al usuario que modifique o permita permisos peligrosos.
Android 8.0 requería que incluyera explícitamente aplicaciones privilegiadas en la lista de permitidos en los archivos XML de configuración del sistema en el directorio /etc/permissions . En Android 9 y superior, los permisos privilegiados deben estar en la lista de permitidos o el dispositivo no puede arrancar.
Para limitar la visibilidad interna de la API y evitar que las aplicaciones accedan accidentalmente a las bibliotecas de la plataforma, Android 7.0 introdujo espacios de nombres para bibliotecas nativas . Esto separa las bibliotecas del sistema de las bibliotecas de aplicaciones, y los fabricantes de dispositivos pueden agregar sus propias bibliotecas nativas.
A partir de Android 10, las aplicaciones deben tener permisos de firma y consentimiento del usuario para acceder al contenido de la pantalla de un dispositivo . Las aplicaciones privilegiadas que se basan en la funcionalidad de captura silenciosa, como tomar una captura de pantalla, deben usar la clase MediaProjection en su lugar.
Transparencia y privacidad
En Android 6.0 y versiones posteriores, la dirección MAC de fábrica del dispositivo está protegida contra el acceso de proveedores de servicios Wi-Fi y analizadores de paquetes. Las restricciones adicionales a partir de Android 10 limitan el acceso de las aplicaciones a los identificadores de dispositivos (ID) inmutables, a menos que estén en la lista de permitidos para permisos privilegiados . (La sección Conectividad proporciona una discusión relacionada con los Identificadores de dispositivos , ya que esto afecta a los operadores).
En Android 9 y versiones anteriores, los usuarios toman decisiones persistentes al otorgar acceso a la ubicación a las aplicaciones. A partir de Android 10, una función de permisos de ubicación de tres estados brinda a los usuarios tres opciones para permitir el acceso de la aplicación a la ubicación de un dispositivo. Estos requisitos de permisos se aplican a las aplicaciones en Android 10 independientemente del SDK de destino.
Configurar permisos para otras funciones de transparencia y privacidad a partir de Android 10
- El recordatorio de ubicación de acceso en segundo plano muestra a los usuarios cuando una aplicación accede a la ubicación de su dispositivo usando el permiso
ACCESS_FINE_LOCATIONen segundo plano. - Se accede a los datos relacionados con la afinidad de contactos, administrados por el componente Proveedor de contactos, de manera diferente: las aplicaciones no pueden escribir ni leer en los datos de afinidad de contactos en la base de datos. Esto afecta las API relacionadas con la persona que llama.
Configuraciones optimizadas
Las configuraciones de permisos se han simplificado para Android 6.0 y versiones posteriores.
- Las capacidades ambientales para los servicios lanzados por
initmantienen todos los aspectos de la configuración del servicio en un único archivo.rc. Al configurar capacidades para servicios no iniciados porinit, configure las capacidades del sistema de archivos usandofs_config.cen su lugar. - Android 7.x y versiones anteriores amplían el mecanismo de ID de Android (AID), utilizando un archivo
android_filesystem_config.hespecífico del dispositivo para especificar las capacidades del sistema de archivos y/o AID personalizados del fabricante del dispositivo. Android 8.0 y versiones posteriores admiten un nuevo método para ampliar las capacidades del sistema de archivos . - En Android 8.0, el manejo de los comandos USB se movió de los scripts de
initespecíficos del dispositivo (una sustitución de las capas HAL) a un demonio USB nativo. La interfaz USB HAL debe implementarse en todos los dispositivos que se inicien en Android 8.0 y superior.
