Trusty 是一種安全作業系統 (OS),可為 Android 提供受信任的執行環境 (TEE)。Trusty OS 與 Android OS 採用相同的處理器,但 Trusty 會透過硬體和軟體與系統的其餘部分隔離。Trusty 和 Android 會平行執行。Trusty 可存取裝置主處理器和記憶體的完整效能,但完全獨立。Trusty 的隔離機制可保護它免受使用者安裝的惡意應用程式,以及 Android 中潛在安全漏洞的影響。
Trusty 與 ARM 和 Intel 處理器相容。在 ARM 系統上,Trusty 會使用 ARM 的 TrustZone 虛擬化主要處理器,並建立安全的 TEE。Intel x86 平台也提供類似支援,使用 Intel 的虛擬化技術即可。
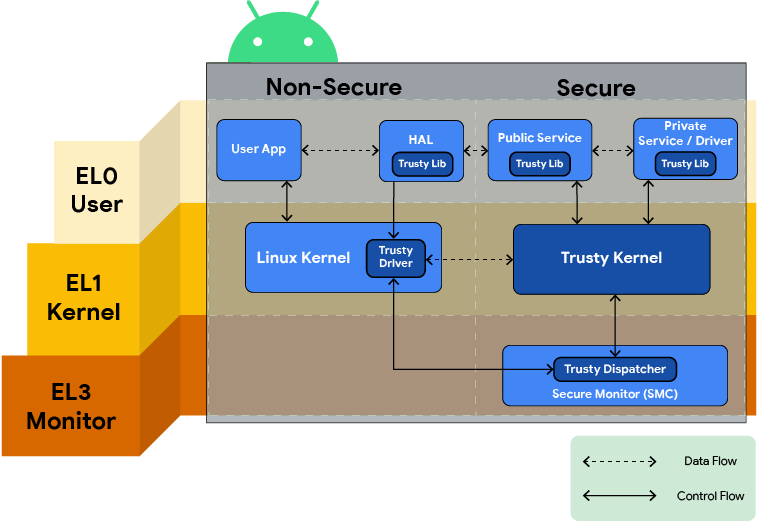
圖 1. Trusty 總覽圖。
Trusty 包含:
- 衍生自 Little Kernel 的小型 OS 核心
- Linux 核心驅動程式,用於在安全環境和 Android 之間傳輸資料
- Android 使用者空間程式庫,可透過核心驅動程式與受信任的應用程式 (即安全工作和服務) 通訊
注意:Trusty 和 Trusty API 可能會變更。如要瞭解 Trusty API,請參閱 Trusty API 參考資料。
Trusty 的優點
其他 TEE 作業系統通常由第三方供應商以二進位大型物件形式提供,或由內部開發。對晶片系統 (SoC) 供應商和原始設備製造商 (OEM) 而言,開發內部 TEE 系統或向第三方授權 TEE 可能所費不貲。貨幣成本加上不可靠的第三方系統,為 Android 創造了不穩定的生態系統。Trusty 是提供給合作夥伴的免費開放原始碼替代方案,可做為 TEE 的可靠選擇。Trusty 提供封閉原始碼系統無法達成的透明度。
Android 支援各種 TEE 實作方式,因此您不一定要使用 Trusty。每個 TEE OS 部署信任應用程式的方式都不盡相同。對於想確保應用程式能在所有 Android 裝置上運作的信任應用程式開發人員來說,這種情況可能會造成問題。應用程式開發人員可將 Trusty 視為標準,建立及部署應用程式,不必考慮多個 TEE 系統的片段化問題。Trusty TEE 可為開發人員和合作夥伴提供透明度、協作功能、程式碼檢查功能,以及簡單明瞭的偵錯功能。可信的應用程式開發人員可以採用通用工具和 API,降低導入安全漏洞的風險。這些開發人員有信心開發應用程式,並在多部裝置上重複使用,不需進一步開發。
應用程式與服務
Trusty 應用程式是一組二進位檔案 (可執行檔和資源檔)、二進位資訊清單和密碼編譯簽章。在執行階段,Trusty 應用程式會以無權限模式,在 Trusty 核心下以獨立程序的形式執行。每個程序都會在自己的虛擬記憶體沙箱中執行,並使用 TEE 處理器的記憶體管理單元功能。硬體建構會改變 Trusty 遵循的確切程序,但舉例來說,核心會使用以安全計時器刻度為基礎的優先順序循環排程器,排程這些程序。所有 Trusty 應用程式的優先順序都相同。
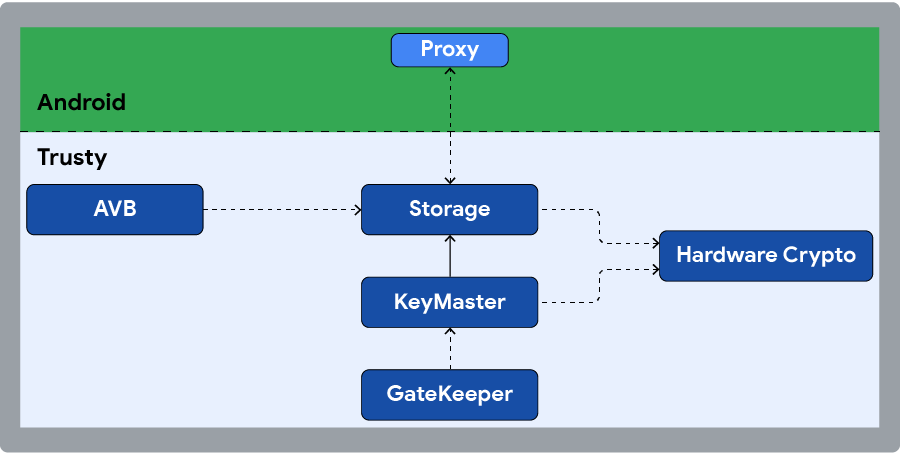
圖 2. Trusty 應用程式總覽。
第三方 Trusty 應用程式
所有 Trusty 應用程式都由單一機構開發,並與 Trusty 核心映像檔一起封裝。 開機時,系統啟動載入程式會簽署並驗證整個映像檔。Trusty 不支援第三方應用程式開發。雖然 Trusty 可用於開發新應用程式,但請務必謹慎行事,因為每個新應用程式都會擴大系統的信任運算基礎 (TCB) 範圍。受信任的應用程式可以存取裝置密碼,並使用這些密碼執行運算或資料轉換。開發可在 TEE 中執行的全新應用程式,為創新開創許多可能性。不過,根據 TEE 的定義,這些應用程式必須附上某種形式的信任聲明,才能發布。這是指應用程式執行所在產品的使用者信任的實體所提供的數位簽章。
用途和範例
TEE 正在成為行動裝置的標準。使用者越來越仰賴行動裝置處理日常事務,因此對安全性的需求也日益增加。與沒有 TEE 的行動裝置相比,有 TEE 的行動裝置更安全。
在實作 TEE 的裝置上,主處理器通常稱為「不信任」,也就是無法存取 RAM、硬體暫存器和一次性熔絲的特定區域,製造商會在這些區域儲存機密資料 (例如裝置專屬的加密金鑰)。在主處理器上執行的軟體會將任何需要使用私密資料的作業,委派給 TEE 處理器。
在 Android 生態系統中,最廣為人知的例子是受保護內容的 DRM 架構。在 TEE 處理器上執行的軟體可以存取解密受保護內容所需的裝置專屬金鑰。主處理器只會看到加密內容,因此能提供高安全等級,防範軟體式攻擊。
TEE 的其他用途包括行動支付、安全銀行業務、多重驗證、裝置重設保護、受重播攻擊保護的持續性儲存空間、安全 PIN 碼和指紋處理,甚至是惡意軟體偵測。
