内存不安全
内存安全 bug 和以原生编程语言处理内存时遇到的错误是 Android 代码库中最常见的问题。此类问题造成了超过 60% 的高严重程度安全漏洞,并造成了数百万次用户可见的崩溃。
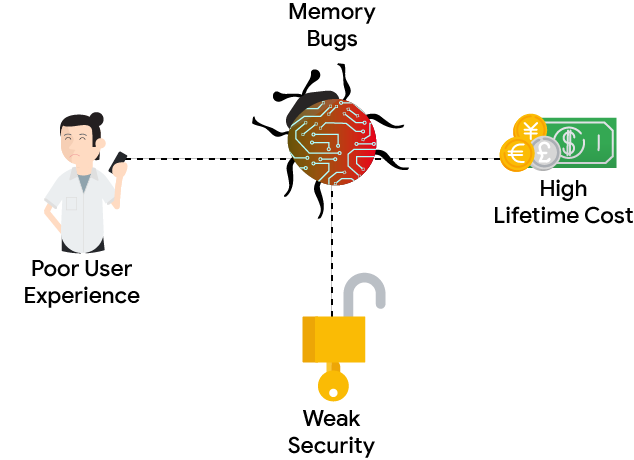
内存安全 bug 会对质量和稳定性产生负面影响,并导致很大一部分在最终用户设备上观测到的崩溃。因此,高密度的内存安全 bug 与糟糕的用户体验直接相关。
使用 C、C++ 和汇编语言等非内存安全型语言编写的原生代码在 Android 平台代码中所占的比例超过 70%,在 Google Play 商店应用中所占的比例大约为 50%。
随着代码的复杂性不断增长,如果一直坐视不管,则内存安全 bug 的数量将随着时间的推移而持续增加。因此,为我们的生态系统提供可检测并缓解此类 bug 的工具和技术对于我们的长期成功至关重要。
在过去的几年里,我们一直与硬件合作伙伴密切合作,开发诸如 Arm 内存标记之类的硬件技术,并在 Android 代码库中引入了 Rust。
这些技术将加速我们的内存安全进程,并且将帮助更广泛的软件行业解决关键问题。
内存安全 bug 会对质量产生负面影响
潜在的内存安全 bug 可能会导致不确定的结果,具体取决于系统的状态。这种不可预测的行为会给我们的用户带来崩溃和困扰。
每天,我们都会观测到来自最终用户设备的数百万次原生代码崩溃,而且随着 GWP-ASan 的引入,我们能够跟踪其中大多数崩溃和内存安全 bug。
此数据点验证了质量与内存安全 bug 密度之间的相关性,并且与我们的 Chrome 同事观测到的结果相一致(请参阅 Chrome GWP-ASan bug 热门表)。
内存安全 bug 会对安全性产生负面影响
从第一个 Android 版本开始,内存安全 bug 就一直是 Android 安全漏洞的首要原因。
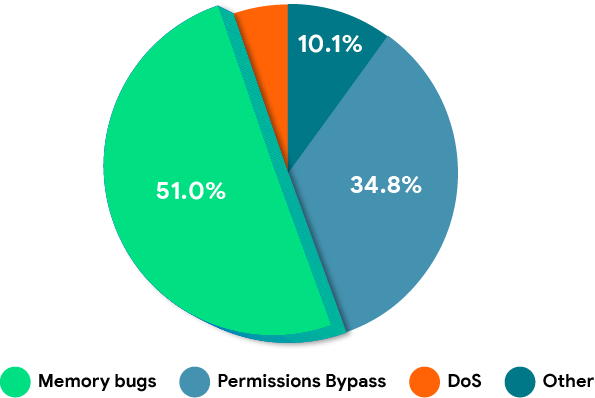
略显欣慰的是,并不是只有 Android 上会发生此问题(参见 Chrome 和 Microsoft 统计信息),但我们仍然需要采取更多措施来保障用户安全。
Google 的 Project Zero 团队负责跟踪针对零日漏洞发起的真实零日攻击。这些 bug 并非虚构的 bug,而是针对用户发起的攻击中使用的有效漏洞。内存安全 bug(内存损坏和释放后使用)构成了绝大多数问题。
内存安全 bug 会导致成本增加
通过安全修复程序及时更新设备可以确保用户安全,但同时也会为我们的生态系统带来资金成本。
低级别供应商代码(通常包含自定义修改)中的高密度内存安全 bug 会显著增加修复和测试成本。 不过,在开发周期的早期阶段检测到这些 bug 可以降低这些成本。
研究表明,尽早检测到 bug 可将成本降低多达六倍。不过,考虑到生态系统的复杂性、供应商维护的平均代码库数量以及日益复杂的软件,节省的成本可能会更高。
内存安全
从 Android 12 开始,我们已经通过多项系统性更改降低了 Android 代码库中的内存安全 bug 密度。 我们将扩展 Android 内存安全工具并引入一些新的要求,以鼓励我们的生态系统处理此类 bug。随着时间的推移,这些工作应能为用户提供更高的质量和更好的安全性,同时降低供应商的成本。
在未来几年内,内存安全可能会成为保证质量和安全性的差异化因素,而 Android 计划引领这一趋势。
内存安全支持方面的要求
Android 兼容性定义文档 (CDD) 强烈建议在开发过程中使用内存安全工具。
我们正在与生态系统密切合作,推动增加内存安全工具的使用,并将该工具集成到持续集成和测试流程中。
我们会逐步确保每台设备均通过使用内存安全工具的完整兼容性测试套件 (CTS) 测试,通过这项测试即表示未发现此类 bug。例如,Arm v9 平台将需要通过启用内存标记的 CTS 测试,而 Arm v8 平台将需要通过使用 HWASAN 和 KASAN 的 CTS 测试。
Rust 作为平台代码的新编程语言
Android 12 引入了 Rust 作为平台语言。Rust 能够以类似于 C/C++ 的性能提供内存和线程安全性。我们预计 Rust 将成为大多数新原生项目的首选语言。 不过,在 Rust 中重写所有内存不安全的代码(目前占 Android 平台代码的 70% 以上)并不可行。 展望未来,Rust 将为内存安全工具提供有力的补充。
内存安全工具
Android 支持各种有助于检测内存安全 bug 的工具。 下图展示了可用 Android 内存安全工具的分类。
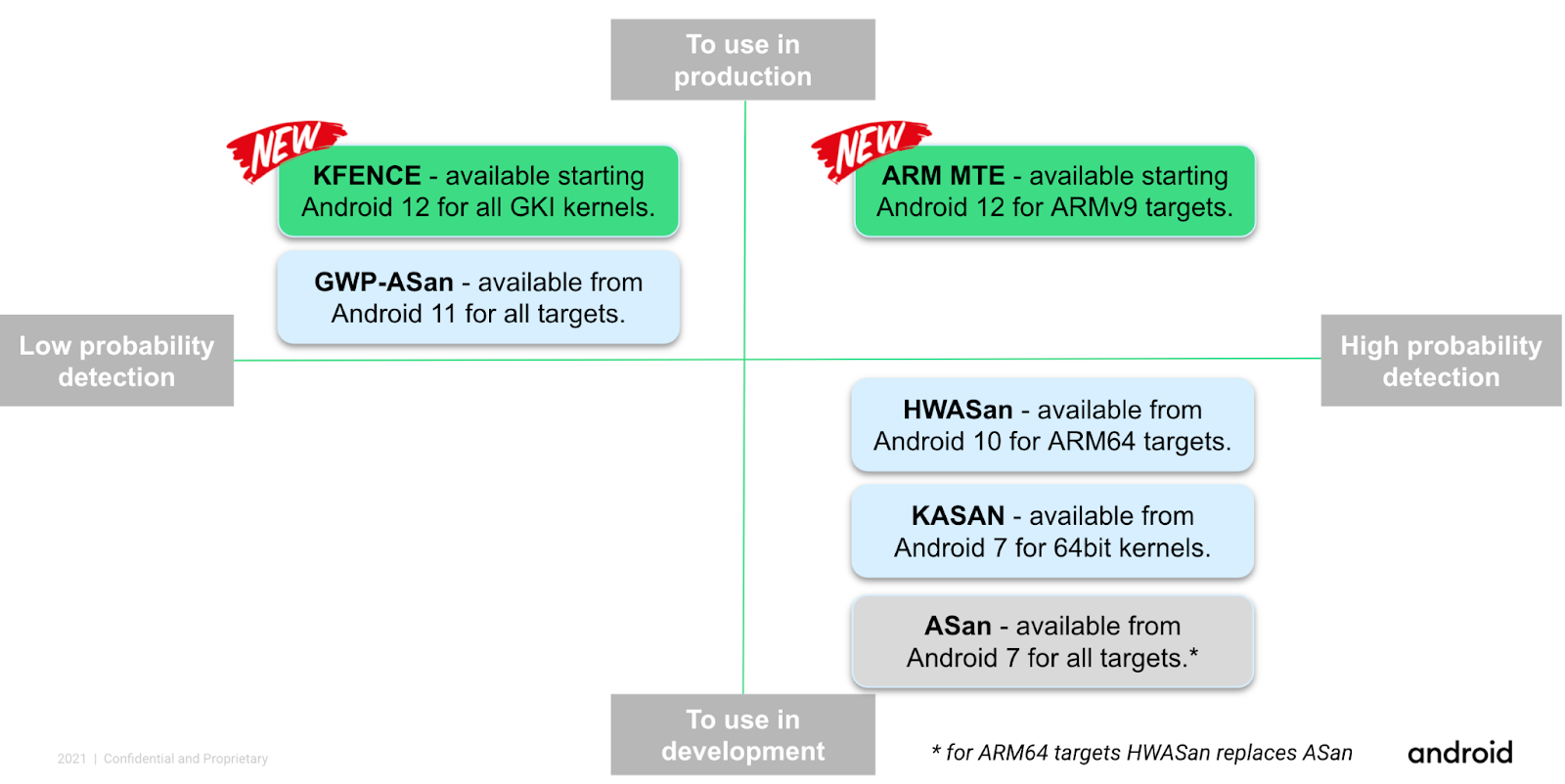
我们的工具涵盖大量部署场景和目标。以下文档介绍了每种工具,并提供了关于如何在您的产品中使用这些工具的参考信息。
