Trusty is a secure operating system (OS) that provides a Trusted Execution Environment (TEE) for Android. The Trusty OS runs on the same processor as the Android OS, but Trusty is isolated from the rest of the system by both hardware and software. Trusty and Android run parallel to each other. Trusty has access to the full power of a device's main processor and memory but is completely isolated. Trusty's isolation protects it from malicious apps installed by the user and potential vulnerabilities in Android.
Trusty is compatible with ARM and Intel processors. On ARM systems, Trusty uses ARM's TrustZone to virtualize the main processor and create a secure TEE. Similar support is also available on Intel x86 platforms using Intel's Virtualization Technology.
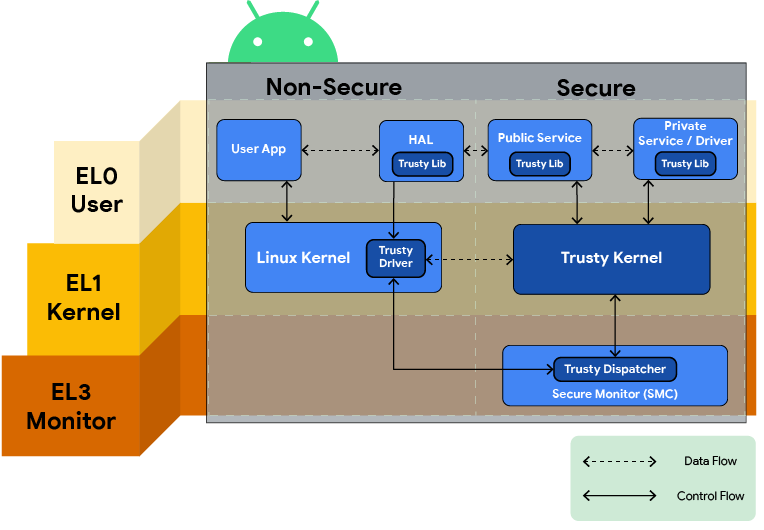
Figure 1. Trusty overview diagram.
Trusty consists of:
- A small OS kernel derived from Little Kernel
- A Linux kernel driver to transfer data between the secure environment and Android
- An Android userspace library to communicate with trusted apps (that is, secure tasks and services) through the kernel driver
Note: Trusty and the Trusty API are subject to change. For information about the Trusty API, see Trusty API reference.
Advantages of Trusty
Other TEE operating systems are traditionally supplied as binary blobs by third-party vendors or developed internally. Developing internal TEE systems or licensing a TEE from a third-party can be costly to system on a chip (SoC) vendors and OEMs. The monetary cost combined with unreliable third-party systems creates an unstable ecosystem for Android. Trusty is provided to its partners as a reliable and free open-source alternative for their TEE. Trusty offers a level of transparency that isn't possible with closed-source systems.
Android supports various TEE implementations so you aren't restricted to using Trusty. Each TEE OS has a unique way of deploying trusted apps. This fragmentation can be a problem for trusted app developers trying to ensure their apps work on every Android device. Using Trusty as a standard helps app developers create and deploy apps without accounting for the fragmentation of multiple TEE systems. Trusty TEE provides developers and partners with transparency, collaboration, inspectability of code, and straighforward debugging. Trusted app developers can converge around common tools and APIs to reduce the risk of introducing security vulnerabilities. These developers have the confidence to develop an app and reuse it across multiple devices without further development.
Apps and services
A Trusty app is a collection of binary files (executables and resource files), a binary manifest, and a cryptographic signature. At run time, Trusty apps run as isolated processes in unprivileged mode under the Trusty kernel. Each process runs in its own virtual memory sandbox using the memory management unit capabilities of the TEE processor. The build of the hardware changes the exact process that Trusty follows, but for example, the kernel schedules these processes using a priority-based, round-robin scheduler driven by a secure timer tick. All Trusty apps share the same priority.
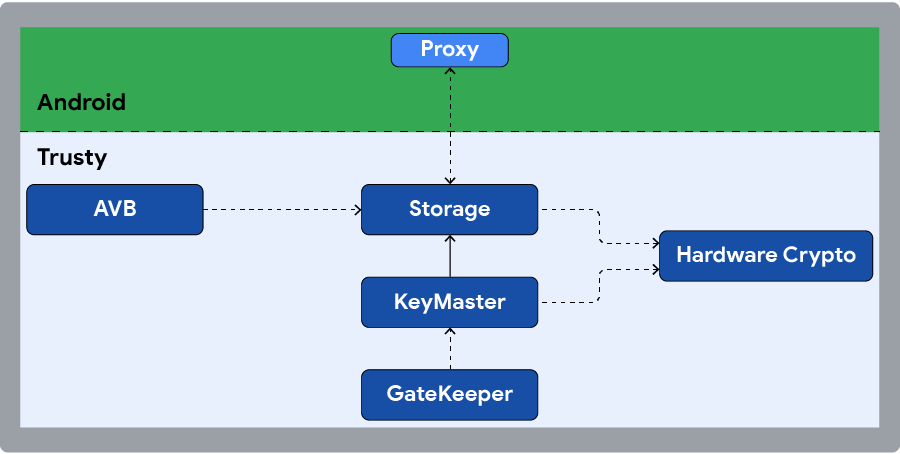
Figure 2. Trusty app overview.
Third-party Trusty apps
All Trusty apps are developed by a single party and packaged with the Trusty kernel image. The entire image is signed and verified by the bootloader during boot. Third-party app development isn't supported in Trusty. Although Trusty enables the development of new apps, do this with extreme care; each new app increases the area of the trusted computing base (TCB) of the system. Trusted apps can access device secrets and can perform computations or data transformations using them. The ability to develop new apps that run in the TEE opens up many possibilities for innovation. However, due to the very definition of a TEE, these apps can't be distributed without some form of trust attached. This is in the form of a digital signature by an entity trusted by the user of the product that the app runs on.
Uses and examples
TEEs are becoming a standard in mobile devices. Users are relying more on their mobile devices for their everyday lives and the need for security is growing. Mobile devices with a TEE are more secure than devices without a TEE.
On devices with a TEE implementation, the main processor is often referred to as *untrusted*, meaning it can't access certain areas of RAM, hardware registers, and write-once fuses where secret data (such as device-specific cryptographic keys) is stored by the manufacturer. Software running on the main processor delegates any operations that require use of secret data to the TEE processor.
The most widely known example of this in the Android ecosystem is the DRM framework for protected content. Software running on the TEE processor can access device-specific keys required to decrypt protected content. The main processor sees only the encrypted content, providing a high level of security and protection against software-based attacks.
TEE has other uses, such as mobile payments, secure banking, multifactor authentication, device reset protection, replay-protected persistent storage, secure PIN and fingerprint processing, and even malware detection.
