根據 Android 相容性定義說明文件,原始設備製造商 (OEM) 必須提供啟用應用程式開發功能的方法。不過,在車內提供類似行動裝置的開發人員選項,會使車輛容易遭到攻擊。原始設備製造商 (OEM) 現在可以使用經過驗證的加密金鑰權杖機制,限制開發人員選項的存取權。具體來說,原始設備製造商可以:
- 在第一次開機前,設定所需的預設限制。
- 安全授權開發人員,並視需要使用加密權杖。
- 在開發人員完成驗證及授權程序後,套用限制變更。
本文將說明參考實作項目,其中包含偵錯限制控制器應用程式和遠端符記發出端點。
術語
除了術語,本文還會使用以下術語:
- JSON Web Signature (JWS),定義於 RFC 7515
- 國家標準暨技術研究院 (NIST)
設計
OEM 廠商可以使用 JSON Web Signature (JWS) 權杖 (RFC7515) 授權開發人員。在參考實作項目中,存取權杖由原始設備製造商 (OEM) 核發,並由限制控制器應用程式使用。存取權杖旨在抵禦重播攻擊和偽造的權杖。
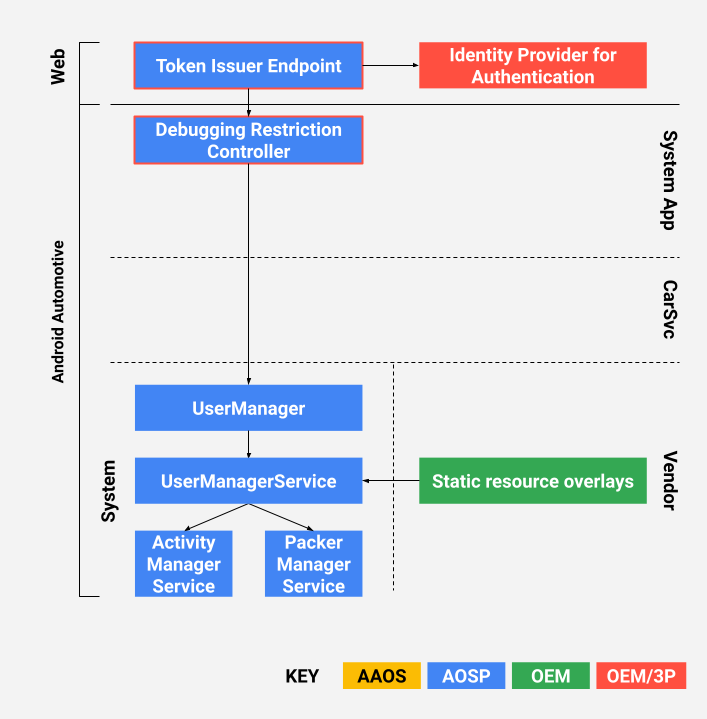
圖 1. 設計
整合和設定
原始設備製造商必須在第一次啟動時指定所需的預設限制。這項操作會使用多個靜態資源疊加層,以便覆寫 Android 開放原始碼計畫架構中的預設值。
無頭系統使用者的預設限制可透過 frameworks/base/core/res/res/values/config.xml 中的 config_defaultFirstUserRestrictions 字串設定,例如:
<!-- User restrictions set when the first user is created.
Note: Also update appropriate overlay files. -->
<string-array translatable="false" name="config_defaultFirstUserRestrictions">
<item>no_debugging_features</item>
</string-array>您可以在 frameworks/base/core/res/res/xml/config_user_types.xml 中設定駕駛人、乘客和隨行者的預設限制。OEM 可以重疊這些字串,為各類型使用者分別設定預設限制,例如:
<user-types> <full-type name="android.os.usertype.full.SECONDARY" > <default-restrictions no_debugging_features="true"/> </full-type> <full-type name="android.os.usertype.full.GUEST" > <default-restrictions no_debugging_features="true"/> </full-type> </user-types>
您可以在 AOSP 的以下位置找到參考實作項目:
packages/apps/Car/DebuggingRestrictionController
測試
Google 建議原始設備製造商 (OEM) 從參考實作開始,然後再進行擴充。
- 在覆蓋檔案中設定所需限制後,請編譯 AAOS 並驗證定義的流程。使用參考應用程式和啟用 JWS 的本機服務,驗證存取設定。
- 設定系統以使用支援 JWS 的雲端服務 (選用)。確認您是否在後端服務中觀察到所需的流程。
