本页将介绍如何启用基于车辆的绑定加密种子功能。
概览
车辆绑定种子功能的主要目标是,通过防止车载信息娱乐系统 (IVI) 中的数据从车辆中移除来进一步保护用户的隐私。具体方法是将存储加密密钥绑定到其他电子控制单元 (ECU),这样,如果 IVI 被移除并放置在另一车辆上(或在测试台上运行),IVI 中经过加密的用户数据便无法解密。
为了绑定文件加密密钥,Vold 会在车辆专用种子中混合使用密钥加密密钥派生函数,以使这些密钥独一无二并实际绑定到车辆。种子是一个字节数组,由原始设备制造商 (OEM) 公开为新的车载硬件抽象层 (VHAL) 属性 STORAGE_ENCRYPTION_BINDING_SEED。该属性的权限受到限制,以使其只能由特权系统守护程序查询。
架构示意图
下图说明了车辆绑定集成的架构:

图 1. 车辆绑定架构。
启用基于车辆的绑定
必须显式启用存储加密与车辆的绑定,并且不能在未恢复出厂设置的情况下开启或关闭此功能。这意味着无线下载 (OTA) 更新在不擦除设备的情况下无法启用此功能。如果 OEM 也将设备恢复出厂设置,则可以选择在升级时启用此功能。例如,在上门服务时。
通过支持供应商提供的车载 HAL 中的 STORAGE_ENCRYPTION_BINDING_SEED 属性,可启用此功能。该属性会保存一个长度为 16 个字节的字节字符串,并且应保留在与 IVI 分开的 ECU 上。该属性最初是由 Android Automotive OS (AAOS) 设置的,后者使用加密安全的随机数字生成器 (CSRNG) 生成该属性。然后,AAOS 会在后续启动时读取该属性。
VHAL 如何存储 STORAGE_ENCRYPTION_BINDING_SEED 的值因供应商而异。我们提供了保护种子的一般性建议:
- (推荐)种子由 ECU 存储在物理上受到良好安全保护的车辆中。如若不然,从车辆中提取 IVI 和 ECU 就变得微不足道了。
- (推荐)IVI 和 ECU 应相互进行身份验证以交换种子,从而防止从 ECU 发出针对种子的仿冒请求。
- (推荐)应使用安全通道传输种子,以防范 CAN 总线嗅探。
此外,请添加以下代码以确保 late-fs 上的供应商 init.target.rc 在 mount_all --late 之前:
# feed vehicle binding seed to vold
exec_start vold_seed_binding车载 HAL 应该在 early_hal(而非 hal now)中开始。无法在 early-hal 中访问任何 persist.* 系统属性,因为尚未装载 /data 分区。
配置基于车辆的绑定
如果 ECU 种子不匹配,设备会重新启动进入恢复模式,并提示用户清除 /data 分区或重试。
您可在 builtins.cpp 中更改提示和擦除数据行为:
- 将
prompt_and_wipe_data更改为wipe_data。系统会擦除设备,然后在不给出提示的情况下重新启动设备。 - 提示消息包含在 recovery.cpp 中。
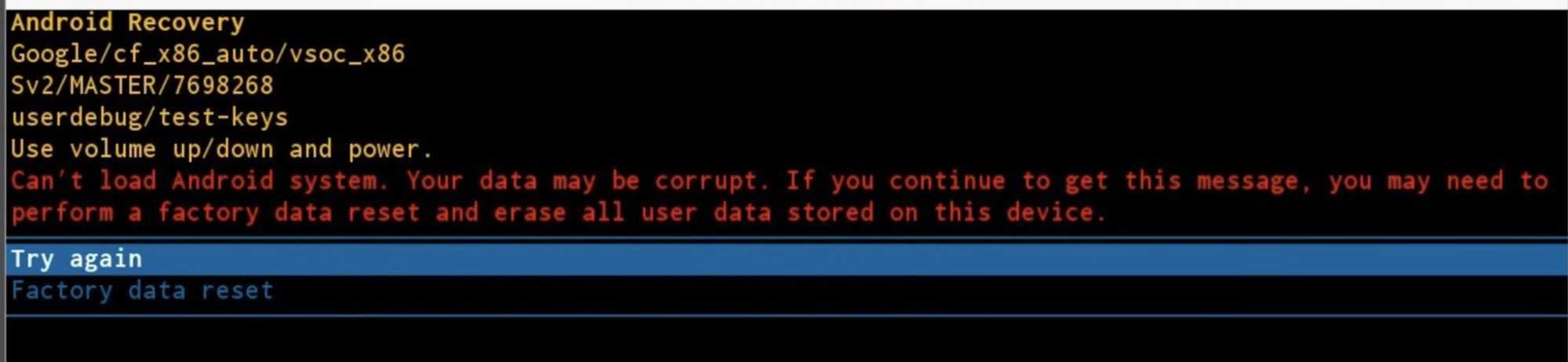
图 2. 提示消息。
测试基于车辆的绑定
模拟测试
packages/services/Car/cpp/security/vehicle_binding_util/tests 中提供了模拟测试。
如需运行此模拟测试,请使用以下命令:
attest libvehicle_binding_util_test
集成测试
packages/services/Car/cpp/security/vehicle_binding_util/tests 中提供了 Atest 测试。
如需运行此集成测试,请使用以下命令:
atest vehicle_binding_integration_test
