為確保車輛系統完整性,Android Automotive 會在以下層級保護傳入的資料:
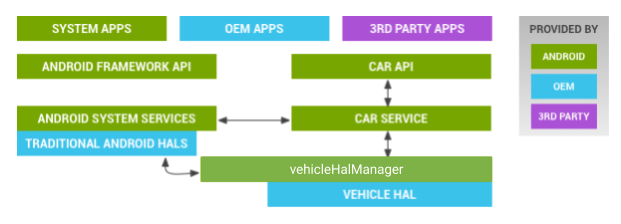
圖 1. 系統服務架構
- 應用程式:系統會驗證應用程式是否有權與 Car 子系統通訊。
- 明確定義的 API。通用 API 不接受任意資料 Blob (API 必須明確定義)。
- 汽車服務。僅允許透過 OTA (或 USB) 進行更新,並採用全磁碟加密和驗證啟動功能。無法側載。
- 車輛 HAL。驗證是否允許特定訊息。
應用程式和 API
Android Automotive 是建構於 Android 之上,可直接與許多攸關安全性的子系統互動。此外,不同車輛可能會提供不同的介面,並向 Android 公開不同的功能。為確保這些功能安全且順暢,我們將這些功能隔離在抽象層中,與 Android 的其他部分分開。只有明確定義的 API 可與車輛 HAL 通訊,這些 API 會對透過車內網路傳送的訊息進行嚴格格式設定。這可為 Android 開發人員提供可預測的介面,並提供與車輛其他部分的安全互動。
車輛 HAL 訊息會經過兩個層級的篩選:
- 應用程式層級:非系統應用程式可透過具備適當權限的車輛服務存取車輛 HAL。
- 車輛 HAL 層級。可提供額外一層防護,確保傳送至車輛子系統的訊息來自合法來源。也可以用來限制訊息傳送頻率,防止惡意應用程式大量傳送訊息,進而干擾車輛子系統。
車輛 HAL
Vehicle HAL 是與車輛互動的較低層,可透過驅動程式輸入/輸出控制 (ioctl) 呼叫,與車內網路和其他車輛硬體通訊。
車輛 HAL 是 Android Automotive 中唯一連線至 IVI 系統的元件,可透過直接應用程式處理器/微控制器連線,或透過 VMCU 限制。車輛 HAL 的存取權應限制在使用 SELinux 規則和核心介面適當權限的系統應用程式。
SELinux 政策
Android Automotive 會擴充 SELinux,用於篩選驅動程式存取權,包括開啟、關閉、讀取、寫入和 ioctl 呼叫。使用 ioctl 篩選 (以及其他 SELinux 功能) 可限制 Vehicle HAL 允許及接受的 CAN 訊息類型,大幅減少攻擊面。如要進一步瞭解 SELinux,請參閱「Android 中的安全增強式 Linux」。
此外,汽車用途包括應隔離及控管的新類型敏感資料。機密資料有獨立的權限;其他功能 (例如 HVAC 控制和視窗調整) 則應只提供給系統應用程式。汽車專屬 SELinux 政策範例:
<permission-group android:name=”android.support.car.permission.CAR_MONITORING /> <permission android:name=”android.support.car.permission.CAR_MILEAGE” android:protectionLevel=”signature|privileged” /> <permission android:name=”android.support.car.permission.CAR_SPEED” android:permissionGroup=”android.permission-group.LOCATION” android:protectionLevel=”dangerous” /> <permission android:name=”android.support.car.permission.CAR_VENDOR_EXTENSION” android:permissionGroup=”android.support.car.permission.CAR_INFORMATION” android:protectionLevel=”signature|privileged” />
CAR_MONITORING 權限群組是為了汽車相關權限而建立。目前的速度可能屬於私密資訊。因此,CAR_SPEED 權限的防護等級為「危險」。這表示資訊屬於私密和敏感資訊。權限 CAR_VENDOR_EXTENSION 是使用系統或簽章層級權限建立,適用於明確授予此權限的系統應用程式或已簽署的應用程式。
應用程式和活動封鎖功能
為減少駕駛時分心,Android Automotive 提供額外控制項 (許可清單),確保車輛行駛時無法使用側載應用程式。這些應用程式在車輛停車或停止時仍可運作。
許可清單會指定車輛行駛時可使用的應用程式。只有可信任的系統應用程式可以更新許可清單。雖然更新可透過網路進行,但不應視為可靠的更新。
