หน่วยความจำที่ไม่ได้เริ่มต้นใน C และ C++ เป็นสาเหตุที่พบบ่อยของปัญหาความน่าเชื่อถือ ข้อบกพร่องด้านความปลอดภัยของหน่วยความจำ และการรั่วไหลของข้อมูล Android จะเริ่มต้นหน่วยความจำให้ได้มากที่สุดเพื่อหลีกเลี่ยงปัญหาเหล่านี้
หน่วยความจําพื้นที่ผู้ใช้ที่เริ่มต้นเป็น 0
ตั้งแต่ Android 12 ระบบจะเริ่มต้นหน่วยความจำสแต็กเป็น 0 ในโค้ดเนทีฟของแพลตฟอร์มทั้งหมด (รวมถึง JNI) และเริ่มต้นหน่วยความจำฮีปเป็น 0 ในกระบวนการเนทีฟของแพลตฟอร์มทั้งหมด (เช่น netd) แต่จะไม่เริ่มต้นใน zygote หรือในแอป
เราขอแนะนำให้แอปของบุคคลที่หนึ่งและแอปของบุคคลที่สามที่สร้างขึ้นด้วย NDK ใช้-ftrivial-auto-var-init=zero Flag คอมไพเลอร์เพื่อเริ่มต้นตัวแปรในกองซ้อนเป็น 0 คอมไพเลอร์จะเพิ่มประสิทธิภาพโดยตัดการใส่ค่า 0 ที่ไม่จำเป็นออก
เช่น เมื่อเริ่มต้นตัวแปรภายในอย่างชัดเจน (เช่น เริ่มต้นตัวแปร int x = 123; x เพียงครั้งเดียว)
หากโปรแกรมมีบัฟเฟอร์สแต็กขนาดใหญ่ในฮอตสปอตด้านประสิทธิภาพ นักพัฒนาซอฟต์แวร์สามารถปิดใช้การเริ่มต้นโดยใช้แอตทริบิวต์คอมไพเลอร์ ดังนี้
__attribute__((__uninitialized__)) char buf[BUFSIZ];
นอกจากนี้ แอปยังเลือกใช้การเริ่มต้นฮีปเป็น 0 ได้ด้วยโดยใช้android:nativeHeapZeroInitializedแอตทริบิวต์ไฟล์ Manifest
หรือจะควบคุมการเริ่มต้น heap 0 ที่รันไทม์ก็ได้ โดยใช้คำสั่งต่อไปนี้
int mallopt(M_BIONIC_ZERO_INIT, level)
โดยที่ระดับคือ 0 หรือ 1
หน่วยความจำเคอร์เนลที่เริ่มต้นค่าเป็น 0
สแต็กเคอร์เนลและกองข้อมูลได้รับการเริ่มต้นค่าเป็น 0 สำหรับเคอร์เนล GKI ซึ่ง CDD แนะนำอย่างยิ่ง
สําหรับการเริ่มต้นสแต็ก GKI จะใช้การกําหนดค่า CONFIG_INIT_STACK_ALL_ZERO ซึ่งจะส่งผลให้สร้างเคอร์เนลโดยใช้ Flag คอมไพเลอร์ -ftrivial-auto-var-init=zero
สําหรับการเริ่มต้นใช้งานฮีป GKI จะใช้ CONFIG_INIT_ON_ALLOC_DEFAULT_ON ซึ่งทําให้การจัดสรรฮีปหน้าเว็บ SLAB และ SLUB ทั้งหมดเริ่มต้นที่ 0 เมื่อสร้าง ตัวเลือกนี้ได้ผลคล้ายกับการส่ง init_on_alloc=1 เป็นตัวเลือกเวลาบูตของเคอร์เนล
รายงานข้อบกพร่อง
เครื่องมือของเราจะสร้างรายงานข้อบกพร่องที่มีประโยชน์ซึ่งมีข้อมูลเพิ่มเติมเพื่อช่วยในการแก้ไขข้อบกพร่อง รายละเอียดการติดตามกองซ้อนของการจัดสรรและการยกเลิกการจัดสรรเพิ่มเติมจะช่วยคุณเข้าใจวงจรชีวิตของการจัดสรรหนึ่งๆ ได้ดียิ่งขึ้น และนำไปสู่การค้นหาข้อบกพร่องด้านความปลอดภัยของหน่วยความจำที่เป็นต้นเหตุได้เร็วขึ้นมาก
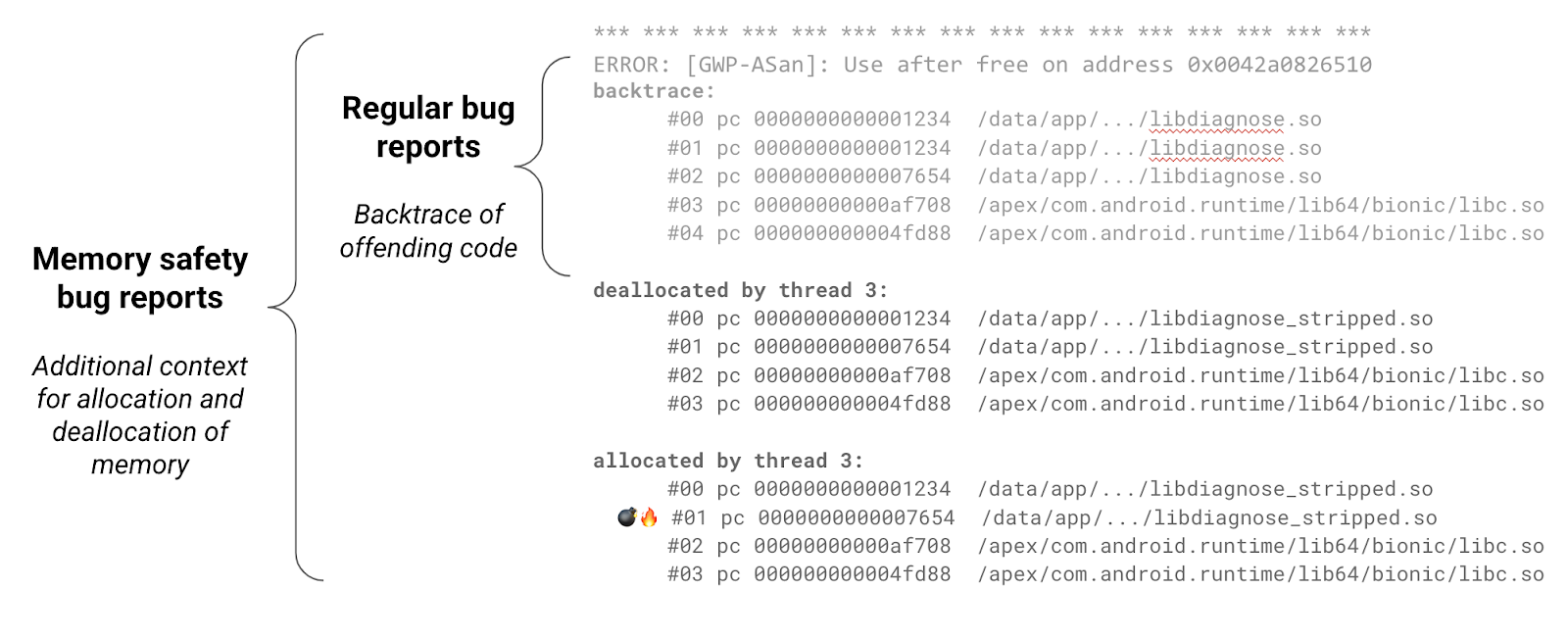
ในระหว่างการพัฒนา ผู้ให้บริการควรตรวจสอบว่ามีข้อบกพร่องหรือไม่โดยตรวจสอบ /data/tombstones และ logcat เพื่อหาข้อขัดข้องที่เกิดขึ้นในอุปกรณ์ ดูข้อมูลเพิ่มเติมเกี่ยวกับการแก้ไขข้อบกพร่องโค้ดเนทีฟของ Android ได้ที่นี่
