L'implementazione degli overlay dell'albero dei dispositivi (DTO) prevede la divisione, la creazione, il partizionamento e l'esecuzione dell'albero dei dispositivi (DT). Una volta implementata una soluzione funzionante, devi anche mantenere la compatibilità tra i due DT e determinare una strategia per garantire la sicurezza di ogni partizione DT.
Dividere il DT
Inizia dividendo il DT in due parti:
- DT principale. La parte solo SoC e le configurazioni predefinite, fornite dal fornitore del SoC.
- Overlay DT. Le configurazioni specifiche del dispositivo, fornite da ODM/OEM.
Dopo aver diviso i DT, devi garantire la compatibilità tra i DT e DT in overlay in modo che l'unione del DT principale e del DT in overlay risulti DT del dispositivo. Per informazioni dettagliate sul formato e sulle regole dei DTO consulta Sintassi DTO. Per maggiori dettagli su più DT, vedi Utilizzare più DT.
Creare DT principali e di overlay
Per creare il DT principale:
- Compila il DT principale
.dtsin un file.dtb. - Esegui il flashing del file
.dtbin una partizione accessibile in fase di esecuzione del bootloader (descritta in [Partition DTs](#partition)).
Per creare la DT di sovrapposizione:
- Compila l'overlay DT
.dtsin un file.dtbo. Sebbene questo formato file sia uguale al file.dtbformattato come DT compresso, l'estensione file diversa lo distingue dal DT principale. - Esegui il flashing del file
.dtboin una partizione accessibile in fase di esecuzione del bootloader (descritta in [Partition DTs](#partition)).
Per informazioni dettagliate sulla compilazione con DTC e sulla verifica dei risultati DTO sull'host, vedi Compilare e verificare.
Partition DTs
Determina una posizione accessibile in fase di runtime e attendibile nel bootloader nella memoria flash in cui inserire .dtb e .dtbo.
Posizioni di esempio per il DT principale:
- Parte della partizione di avvio, aggiunta al kernel (
image.gz) - Blob DT separati (
.dtb) in una partizione dedicata (dtb)
Posizioni di esempio per l'overlay DT:
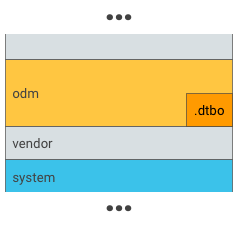
Figura 1. Inserisci .dtbo in una partizione odm (esegui questa operazione solo se il bootloader ha la capacità di caricare i dati dal file system di una partizione odm).
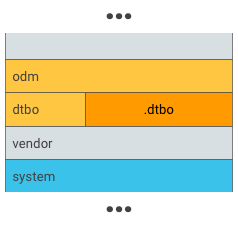
Figura 2. Inserisci .dtbo in una partizione univoca, ad esempio una partizione dtbo.
Nota:le dimensioni della partizione DT di overlay dipendono dal dispositivo e dalla quantità di modifiche necessarie nella parte superiore del blob DT principale. In genere, 8 MB sono più che sufficienti e consentono di aumentare la dimensione in futuro, se necessario.
Per i dispositivi che supportano aggiornamenti (A/B) senza interruzioni, esegui il test A/B delle partizioni DT principale e DT overlay:
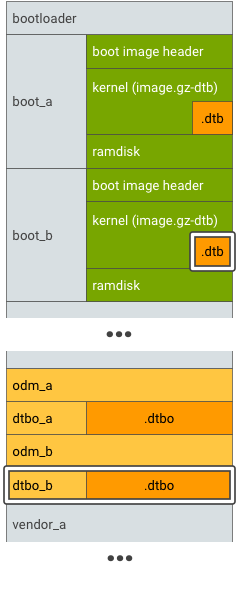
Figura 3. Partizione DTBO A/B, esempio 1.
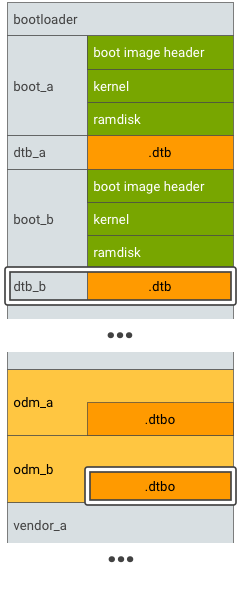
Figura 4. Partizione DTBO A/B, esempio 2.
Esegui nel bootloader
Per eseguire:
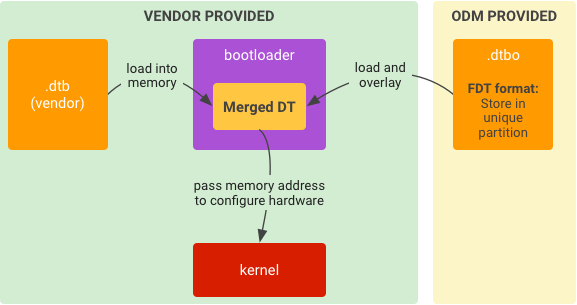
Figura 5. Implementazione tipica del runtime per DTO nel bootloader.
- Carica
.dtbdallo spazio di archiviazione nella memoria. - Carica
.dtbodallo spazio di archiviazione nella memoria. - Sovrapponi
.dtba.dtboper creare un DT unito. - Avvia il kernel dato l'indirizzo di memoria del DT unito.
Mantenere la compatibilità
Il DTB principale (del fornitore del SoC) viene trattato come una superficie API per i DTBO. Dopo aver separato il DT in una parte comune al SoC e una parte specifica del dispositivo, devi mantenere le due parti reciprocamente compatibili in futuro, tra cui:
- Definizione DT nel DT principale. Ad esempio, nodi, proprietà, etichette. Qualsiasi modifica alla definizione nel DT principale potrebbe attivare modifiche nel DT di sovrapposizione. Ad esempio, per correggere il nome di un nodo nel DT principale, definisci un'etichetta "alias" che corrisponda al nome del nodo originale (per evitare la modifica del DT di overlay).
- Overlay della sede del negozio DT. Ad esempio, nome della partizione, formato del negozio.
Garantire la sicurezza
Il bootloader deve garantire che il DTB o il DTBO siano sicuri, non modificati e non danneggiati. Puoi utilizzare qualsiasi soluzione per proteggere DTB o DTBO, ad esempio la firma dell'immagine di avvio in VBoot 1.0 o il piè di pagina HASH di AVB (VBoot 2.0).
- Se DTB o DTBO si trova in una partizione unica, puoi aggiungere questa partizione alla catena di attendibilità di AVB. La catena di attendibilità inizia da una radice di attendibilità protetta dall'hardware e arriva al bootloader, che verifica l'integrità e l'autenticità della partizione DTB o DTBO.
- Se DTB o DTBO si trova in una partizione esistente (ad esempio la partizione
odm), questa partizione deve far parte della catena di attendibilità di AVB. (La partizione DTBO potrebbe condividere una chiave pubblica con la partizioneodm).
Per maggiori dettagli, consulta Avvio verificato.
