對於搭載 Android 13 以上版本的裝置,Android 支援「首次使用時信任」(TOFU) 驗證方法 (RFC7435),使用者只要安裝伺服器使用的根 CA,並在已儲存的網路中設定網域名稱,即可信任企業 (EAP) 網路。TOFU 可讓裝置在使用者首次連上企業網路時取得未經驗證的公開金鑰,並保留該金鑰以供後續連線使用。
背景
與僅需密碼的個人網路相比,企業網路使用公開金鑰基礎架構 (PKI) 驗證,因此用戶端必須預先安裝憑證。在 Android 11 以下版本中,使用者可以在網路設定中選取「不驗證」選項,略過伺服器端憑證的驗證程序。不過,為了加強安全性並符合 WPA R2 規格,Android 12 導入了企業網路必須通過伺服器憑證驗證的規定。這項額外要求為使用者帶來阻礙,因為他們必須為這類網路安裝 CA 憑證。使用者接受 PKI 型企業網路的根 CA 後,即可透過 TOFU 連線至該網路。
功能行為
如果使用者連線至沒有預先安裝已驗證公開金鑰的企業網路,支援 TOFU 的裝置會出現下列行為。
透過 Wi-Fi 選擇器連線至新網路
在 Wi-Fi 選擇器中選取新的企業網路。
裝置會顯示對話方塊 (圖 1),確認網路是否可信任。
輕觸「是,連線」即可接受網路連線,輕觸「否,不要連線」則可拒絕。
輕觸「是,連線」後,裝置會自動設定安全參數、連上網路,並啟用網路的自動連線功能。
如果輕觸「否,不要連線」,裝置就會中斷與網路的連線,並停用該網路的自動連線功能。
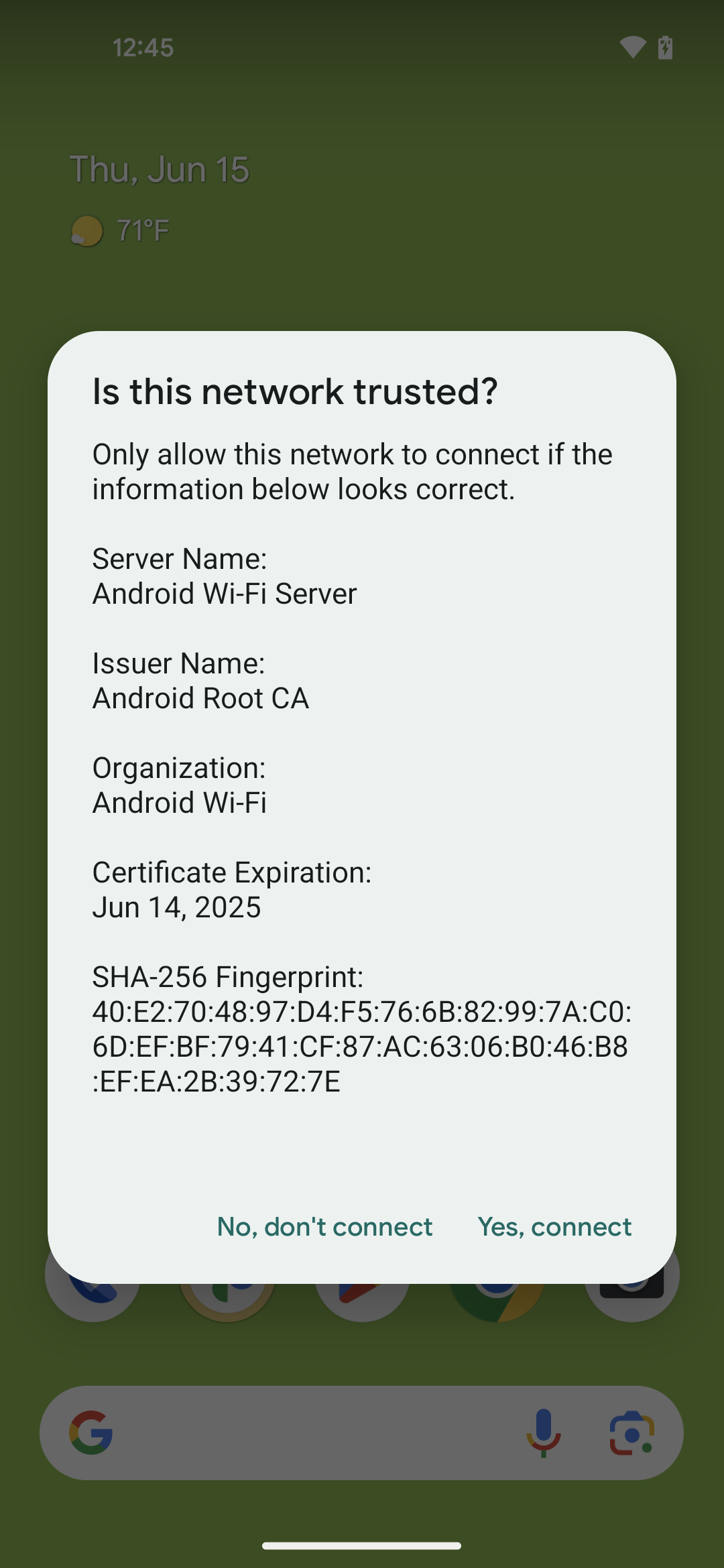
圖 1. TOFU 功能的對話方塊
連線至已啟用自動連線功能的現有網路
連線至已啟用自動連線功能,但沒有有效 CA 憑證的企業網路時,裝置會自動連線,然後顯示無法關閉的通知。
輕觸通知。
裝置會顯示對話方塊 (圖 1),確認網路是否可信任。
輕觸「是,連線」即可接受網路連線,輕觸「否,不要連線」則可拒絕。
輕觸「是,連線」後,裝置會自動設定安全參數、連上網路,並啟用網路的自動連線功能。
如果輕觸「否,不要連線」,裝置就會中斷與網路的連線,並停用該網路的自動連線功能。
實作
如要支援 TOFU 功能,請在 Android 開放原始碼計畫 (AOSP) 中實作供應商 HAL,網址為 /hardware/interfaces/wifi/supplicant/aidl/android/hardware/wifi/supplicant。
Android 13 提供下列公開 API,供應用程式使用:
WifiManager#isTrustOnFirstUseSupported():表示裝置是否支援 TOFU。WifiEnterpriseConfig#enableTrustOnFirstUse(boolean): 啟用 TOFU。WifiEnterpriseConfig#isTrustOnFirstUseEnabled():指出是否已啟用 TOFU。
驗證
如要驗證裝置上的 TOFU 實作,請使用下列測試:
- CTS:
CtsWifiTestCases - VTS:
VtsHalWifiSupplicantStaNetworkTargetTest
