在 Android 6 以上版本中,Wi-Fi 服務供應商和封包分析器已受到限制,無法透過網路要求的 Wi-Fi 堆疊擷取裝置的出廠 MAC 位址。自 Android 10 起,我們已實施額外限制,將裝置 ID 存取權限限制給具備 特權權限層級的應用程式。這麼做可保護裝置 ID,例如
- 電話 IMEI、MEID、ESN 和 IMSI 號碼。
- 版本、SIM 卡或 USB 序號。
誰可以存取裝置 ID
即使應用程式指定 Android 9 以下版本,裝置 ID 仍會受到限制。裝置 ID 可供下列使用者存取:
- 預設的簡訊應用程式。
- 應用程式在
Manifest.permission類別中同時具備READ_PRIVILEGED_PHONE_STATE權限,並在privapp-permission.xml檔案中列入許可清單。這些檔案也必須載入至priv-app目錄。 - 具有電信業者權限的應用程式,如 UICC 電信業者權限所定義。
- 裝置擁有者或設定檔擁有者,且已在
Manifest.permission類別中授予READ_PHONE_STATE權限。(不必加入許可清單)。
特殊權限套件存取權
套件必須具備存取裝置 ID 的權限。該類別必須在 Manifest.permission 類別中具有
READ_PRIVILEGED_PHONE_STATE 權限,並在 privapp-permission.xml 檔案中列入許可清單。如要瞭解許可清單程序,請參閱「特權權限許可清單」。
如要瞭解如何取得非特權套件的專屬 ID,請參閱「 常見用途和適用的適當 ID」。
限制裝置 ID 和隨機 MAC 位址
為進一步限制裝置 ID,Android 10 上的所有裝置預設會為探測和相關聯的要求傳送隨機 MAC 位址,且每個 SSID 都必須有不同的隨機 MAC 位址。請勿在用戶端模式、軟體存取點 (AP) 或 Wi-Fi Direct 用途中使用裝置工廠 MAC 位址。它必須隱藏在非特權應用程式可公開存取的 API 中。需要返回原廠 MAC 位址的特權應用程式必須具備 LOCAL_MAC_ADDRESS 權限。
使用者可以選擇保留為每個 SSID 指派的預設隨機 MAC 位址。您可以在「設定」 >「網路詳細資料」的「隱私權」下方查看這個選項。如要瞭解如何取得隨機 MAC 位址,請參閱「 隨機 MAC 位址」。
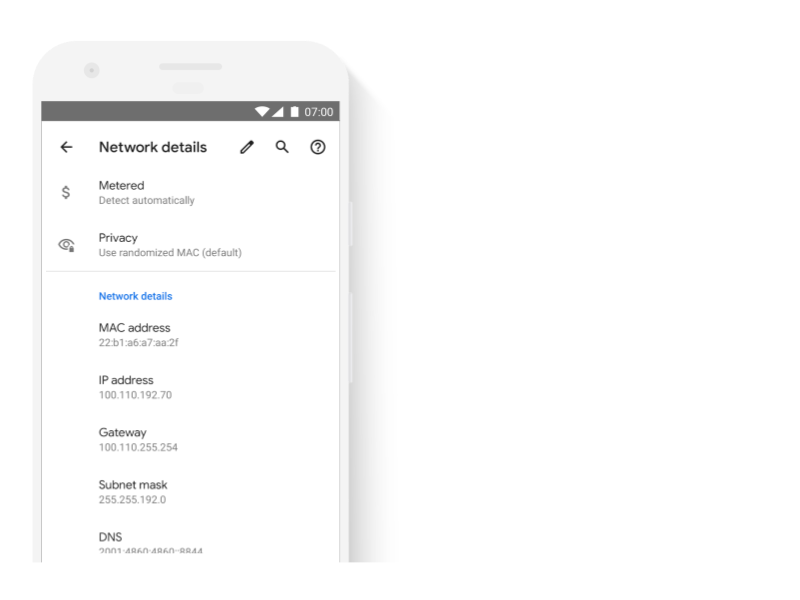
圖 1.「隱私權」的「網路詳細資料」下方顯示 MAC 位址已隨機化。
叫用裝置 ID API 的應用程式
呼叫裝置 ID API 的應用程式必須符合 Android 10 規定。否則,當他們嘗試存取裝置 ID 時,系統會傳回以下內容:
- 鎖定 Android 10 的應用程式
SecurityException會從裝置 ID API 擲回。- 指定 Android 9 以下版本的應用程式
- 如果他們具有
READ_PHONE_STATE權限,則會傳回null回應或預留位置資料。 - 如果不符合要求,裝置 ID API 就會擲回
SecurityException,其中包含所呼叫方法的名稱,以及指出呼叫應用程式不符合存取要求 ID 的條件。
如要進一步瞭解不可變動的裝置 ID,請參閱「不可重設的裝置 ID」和「專屬 ID 的最佳做法」。
測試
應用程式必須禁止存取裝置序號,以及適用情況下的 IMEI 或 MEID、SIM 卡序號和訂閱者 ID。具有存取這些 ID 權限的應用程式,也必須符合「誰可以存取裝置 ID」一節所列的其中一個條件。

