Android 虚拟化框架 (AVF) 提供安全且私密的执行环境来执行代码。AVF 非常适合以安全为导向的用例,这些用例需要比 Android 应用沙盒提供的安全系数更高、甚至经过正式验证的隔离保证。Android 提供了实现 AVF 所需的所有组件的参考实现。目前,只有 ARM64 设备支持 AVF。图 1 显示了 AVF 的架构:
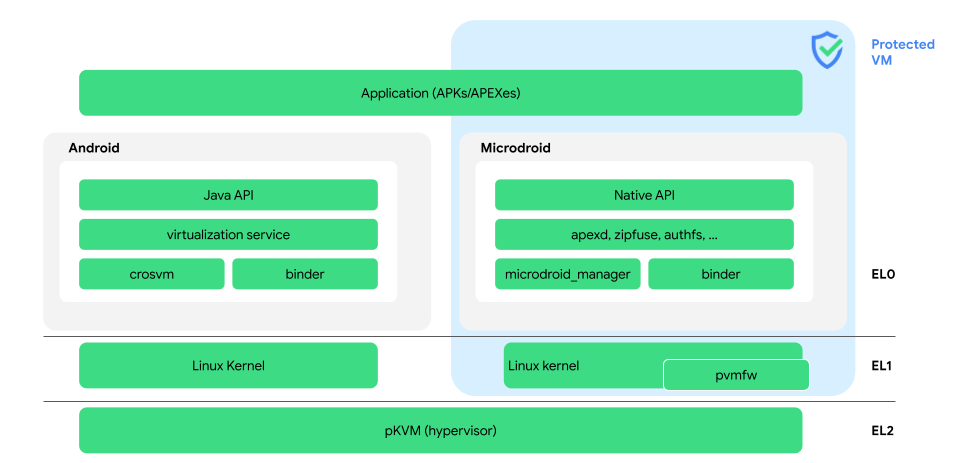
以下是图 1 中最重要的术语的定义:
- apexd 和 zipfuse
- 安全地装载从主机导入的 APEX 和 APK。
- authfs
- 一个融合文件系统,用于在 Android 和 pVM(主机和客户机)之间安全地共享多个文件。
- binder
- 虚拟机间通信的主要方式。
- crosvm
- 一个以 Rust 编写的虚拟机监视器。crosvm 分配虚拟机内存、创建虚拟 CPU 线程,以及实现虚拟设备的后端。
- 通用内核映像 (GKI)
- 经过 Google 认证的启动映像,其中包含基于 Android 通用内核 (ACK) 源代码树构建的 GKI 内核,适合刷写到 Android 设备的启动分区。如需了解详情,请参阅内核概览。
- Hypervisor
- AVF 使用的虚拟化技术,也称为 pKVM。即使主机 Android 或任何其他 pVM 遭到入侵,Hypervisor 仍可保持已执行代码的完整性和 pVM 资源的机密性。
- Java API
- VirtualizationService Java API,仅存在于支持 AVF 的设备上。这些 API 是可选的,不属于
thebootclasspath。 - Microdroid
- Google 提供的在 pVM 中运行的迷你版 Android OS。
- Microdroid 管理器
- 管理 pVM 内的 pVM 生命周期,以及实例磁盘。
- 原生 API
- Android 原生开发者套件 (NDK) 的一个子集。
- 基于内核的受保护虚拟机 (pKVM)
- 请参阅 Hypervisor。
- pVM 固件 (
pvmfw) - 在 pVM 上运行的第一个代码,
pvmfw会验证载荷并推导每个虚拟机的 Secret。 - 受保护的虚拟机 (pVM)
一种互不信任的隔离执行环境(客户机),与主 Android 操作系统(主机)一起运行。pVM 安全的一个重要方面是,即使主机遭到入侵,主机也无法访问 pVM 的内存。pKVM 是运行 pVM 的标准 Hypervisor。
与现有的可信执行环境 (TEE) 相比,pVM 可提供更丰富的环境,包括能够运行一个名为 Microdroid 的迷你版 Android 分发平台(尽管 Microdroid 也可以在未受保护的虚拟机上运行)。pVM 可以动态使用,并且在可信环境中提供一组标准 API,供所有支持它们的设备使用。
- VirtualizationService
管理 pVM 生命周期的 Android 服务。
后续操作
- 如果您想更好地了解对 AVF 的需求,请参阅为什么选择 AVF?
- 如需了解如何使用 AVF 进行隔离编译,请参阅用例。
- 如果您想更深入地了解 AVF 参考实现的架构,请参阅 AVF 架构。
- 如果您想了解 Microdroid,请参阅 Microdroid。
- 如果您对 AVF 如何处理安全性事宜感兴趣,请参阅安全性。
- 如需了解虚拟化服务的作用,请参阅 VirtualizationService。
- 如需了解 AVF 的源代码或有关各个组件的深入说明,请参阅 AOSP 代码库
