สำหรับอุปกรณ์ที่ใช้ Android 13 ขึ้นไป Android รองรับแนวทางการตรวจสอบสิทธิ์แบบเชื่อถือเมื่อใช้งานครั้งแรก (TOFU) (RFC7435) ซึ่งช่วยให้ผู้ใช้เชื่อถือเครือข่ายขององค์กร (EAP) ได้โดยการติดตั้ง CA ระดับรูท ที่เซิร์ฟเวอร์ใช้และตั้งชื่อโดเมนในเครือข่ายที่บันทึกไว้ TOFU ช่วยให้อุปกรณ์รับคีย์สาธารณะที่ไม่ได้รับการตรวจสอบสิทธิ์ได้เมื่อผู้ใช้เชื่อมต่อกับเครือข่ายขององค์กรเป็นครั้งแรก และเก็บคีย์ไว้สำหรับการเชื่อมต่อครั้งต่อๆ ไป
ฉากหลัง
เมื่อเทียบกับเครือข่ายส่วนตัวที่ต้องใช้รหัสผ่านเท่านั้น เครือข่ายขององค์กร ใช้การตรวจสอบสิทธิ์โครงสร้างพื้นฐานของคีย์สาธารณะ (PKI) ซึ่งกำหนดให้ไคลเอ็นต์ ต้องติดตั้งใบรับรองล่วงหน้า ใน Android 11 หรือต่ำกว่า ผู้ใช้สามารถเลือกตัวเลือกไม่ตรวจสอบสำหรับใบรับรอง CA ของเซิร์ฟเวอร์ในการตั้งค่าเครือข่าย โดยข้ามการตรวจสอบใบรับรองฝั่งเซิร์ฟเวอร์ อย่างไรก็ตาม Android 12 ได้กำหนดให้เครือข่ายขององค์กรต้องมีการตรวจสอบใบรับรองเซิร์ฟเวอร์เพื่อเสริมความปลอดภัยและปฏิบัติตามข้อกำหนด WPA R2 ข้อกำหนดเพิ่มเติมนี้ สร้างอุปสรรคสำหรับผู้ใช้เนื่องจากต้องติดตั้งใบรับรอง CA สำหรับเครือข่ายดังกล่าว TOFU ช่วยให้ผู้ใช้เชื่อมต่อกับเครือข่ายองค์กรที่ใช้ PKI ได้โดยการยอมรับ CA หลัก
ลักษณะการทำงาน
อุปกรณ์ที่รองรับ TOFU จะแสดงลักษณะการทำงานต่อไปนี้เมื่อผู้ใช้เชื่อมต่อ กับเครือข่ายขององค์กรที่ไม่มีติดตั้ง คีย์สาธารณะที่ตรวจสอบสิทธิ์แล้ว
เชื่อมต่อกับเครือข่ายใหม่ผ่านตัวเลือก Wi-Fi
เลือกเครือข่ายองค์กรใหม่ในตัวเลือก Wi-Fi
อุปกรณ์จะแสดงกล่องโต้ตอบ (รูปที่ 1) เพื่อยืนยันว่า เครือข่ายเชื่อถือได้หรือไม่
แตะใช่ เชื่อมต่อเพื่อยอมรับการเชื่อมต่อเครือข่าย หรือแตะไม่ ไม่ต้องเชื่อมต่อเพื่อปฏิเสธ
หากแตะใช่ เชื่อมต่อ อุปกรณ์จะกำหนดค่า พารามิเตอร์ความปลอดภัยโดยอัตโนมัติ เชื่อมต่อกับเครือข่าย และเปิดใช้การเชื่อมต่ออัตโนมัติ สำหรับเครือข่าย
หากแตะไม่ ไม่ต้องเชื่อมต่อ อุปกรณ์จะตัดการเชื่อมต่อจากเครือข่ายและปิดใช้การเชื่อมต่ออัตโนมัติสำหรับเครือข่าย
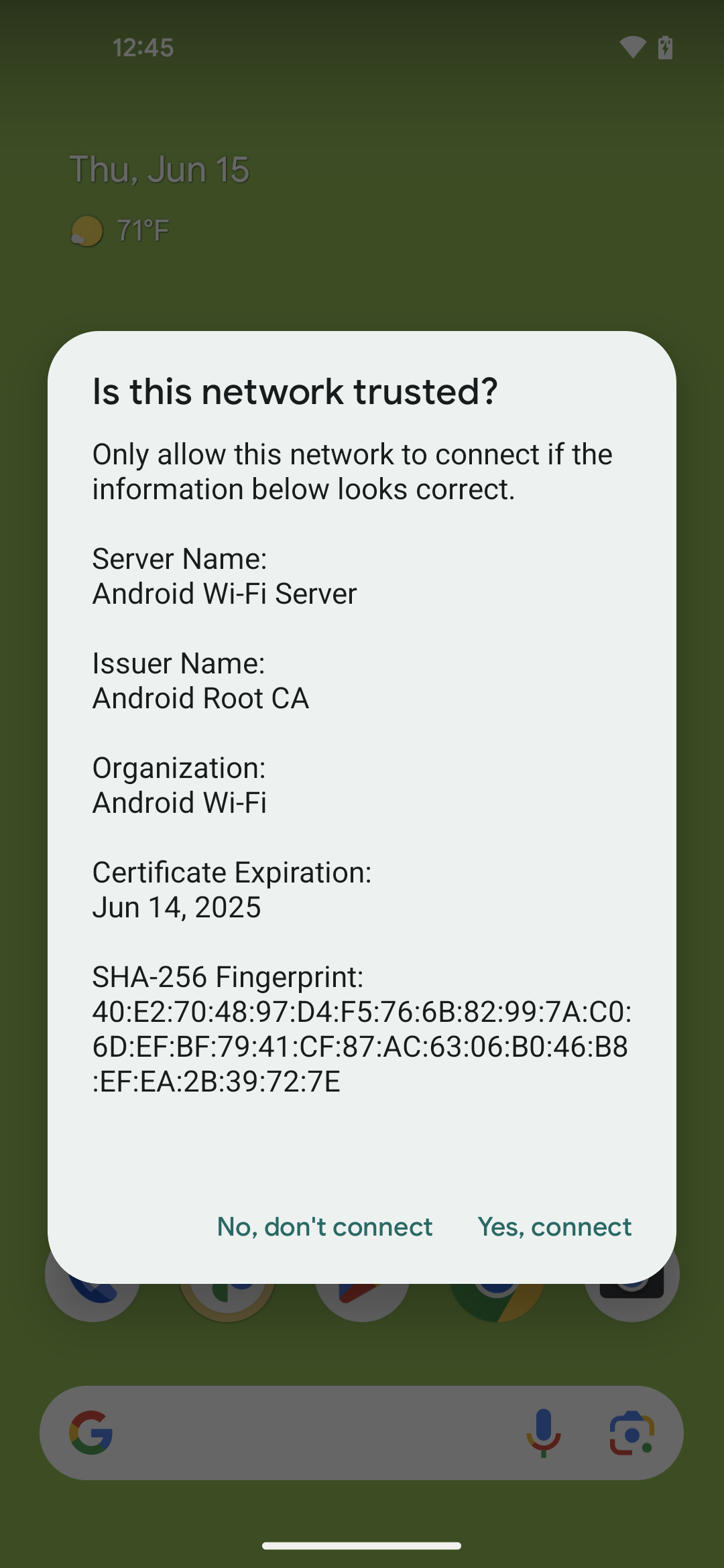
รูปที่ 1 กล่องโต้ตอบสำหรับฟีเจอร์ TOFU
เชื่อมต่อกับเครือข่ายที่มีอยู่โดยเปิดใช้การเชื่อมต่ออัตโนมัติ
เมื่อเชื่อมต่อกับเครือข่ายขององค์กรที่เปิดใช้การเชื่อมต่ออัตโนมัติแต่ ไม่มีใบรับรอง CA ที่ถูกต้อง อุปกรณ์จะเชื่อมต่อโดยอัตโนมัติ จากนั้น จะแสดงการแจ้งเตือนแบบเหนียว (ปิดไม่ได้)
แตะการแจ้งเตือน
อุปกรณ์จะแสดงกล่องโต้ตอบ (รูปที่ 1) เพื่อยืนยันว่า เครือข่ายเชื่อถือได้หรือไม่
แตะใช่ เชื่อมต่อเพื่อยอมรับการเชื่อมต่อเครือข่าย หรือแตะไม่ ไม่ต้องเชื่อมต่อเพื่อปฏิเสธ
หากแตะใช่ เชื่อมต่อ อุปกรณ์จะกำหนดค่า พารามิเตอร์ความปลอดภัยโดยอัตโนมัติ เชื่อมต่อกับเครือข่าย และเปิดใช้การเชื่อมต่ออัตโนมัติ สำหรับเครือข่าย
หากแตะไม่ ไม่ต้องเชื่อมต่อ อุปกรณ์จะตัดการเชื่อมต่อจากเครือข่ายและปิดใช้การเชื่อมต่ออัตโนมัติสำหรับเครือข่าย
การใช้งาน
หากต้องการรองรับฟีเจอร์ TOFU ให้ใช้ HAL ของ Supplicant ที่ระบุไว้ใน
โครงการโอเพนซอร์ส Android (AOSP) ที่
/hardware/interfaces/wifi/supplicant/aidl/android/hardware/wifi/supplicant
API สาธารณะต่อไปนี้พร้อมใช้งานใน Android 13 สำหรับแอป
WifiManager#isTrustOnFirstUseSupported(): ระบุว่าอุปกรณ์รองรับ TOFU หรือไม่WifiEnterpriseConfig#enableTrustOnFirstUse(boolean): เปิดใช้ TOFUWifiEnterpriseConfig#isTrustOnFirstUseEnabled(): ระบุว่าเปิดใช้ TOFU หรือไม่
การตรวจสอบความถูกต้อง
หากต้องการตรวจสอบการติดตั้งใช้งาน TOFU ในอุปกรณ์ ให้ใช้การทดสอบต่อไปนี้
- CTS:
CtsWifiTestCases - VTS:
VtsHalWifiSupplicantStaNetworkTargetTest
