Android 权限系统提供的控件可提高用户对应用权限的认知,还可以限制应用对敏感数据的访问。在 Android 8.0 及更低版本中,权限配置包括将应用列入许可名单。特权应用如果未列入许可名单,即使位于 priv-app 路径中,也一样会被停用。在 Android 9 及更高版本上,如果设备尝试使用未正确列入许可名单的应用,则系统将无法启动。
Android 10 引入了角色的概念,这是系统中与某些要求和特权关联的独特名称。为应用分配角色以授予其针对特定用途的权限,并使用平台配置资源配置默认角色。
这些针对潜在有害应用 (PHA) 的增强型防护措施有助于:
- 更好地了解可能有害的应用的行为。
- 加强用户对应用行为的控制。
- 让应用开发者在使用受权限保护的私人数据时更加谨慎。
软件包安装和权限
在 Android 9 及更低版本中,软件包安装和权限控制功能包含在 PackageInstaller 软件包 (//packages/apps/PackageInstaller) 中。在 Android 10 及更高版本中,权限控制功能位于单独的软件包 PermissionController (//packages/apps/PermissionController) 中。图 1 显示了这两个软件包在 Android 10 中的位置。
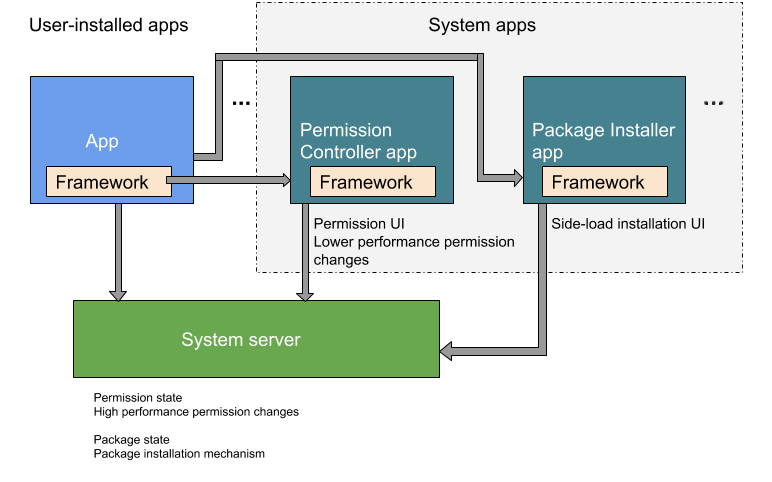
图 1. Android 10 中的软件包安装和权限控制功能
许可名单和访问权限
在 Android 6.0 及更高版本中,应用会在运行时申请危险权限。 Android 10 增加了具备活动识别 (AR) 能力的运行时权限机制,可提示用户修改或允许危险权限。
Android 8.0 要求您在系统配置 XML 文件(位于 /etc/permissions 目录下)中明确将特权应用列入许可名单。在 Android 9 及更高版本中,特许权限必须列入许可名单,否则设备无法启动。
为了限制内部 API 的可见性并防止应用意外地访问平台库,Android 7.0 推出了针对原生库的命名空间。这将系统库与应用库分离开来,而设备制造商可以添加自己的原生库。
从 Android 10 开始,应用必须拥有签名权限并征得用户同意才能访问设备的屏幕内容,两者缺一不可。依赖于静默捕获功能(如截取屏幕截图)的特权应用应改为使用 MediaProjection 类。
Android 15 要求您:在 /etc/permissions 目录下的系统配置 XML 文件中,明确将那些由非系统应用请求或由系统应用更新最新请求的平台签名权限列入许可名单。
透明度和隐私权
Android 6.0 及更高版本会阻止 Wi-Fi 服务提供方和数据包分析器访问设备的出厂 MAC 地址。自 Android 10 起,还有其他一些限制条件会限制应用访问不可变设备标识符 (ID),除非相应应用已列入特许权限许可名单。(连接部分提供了有关设备标识符的相关讨论,因为运营商会受其影响)。
在 Android 9 及更低版本中,用户在向应用授予位置信息访问权限时做出的选择是永久性的。从 Android 10 开始,三态位置信息权限功能为用户提供了三个选项,用来控制应用如何访问设备的位置信息。无论目标 SDK 设置如何,这些权限要求都适用于 Android 10 中的应用。
从 Android 10 开始,您需要配置其他透明度和隐私权功能的权限
- 当某个应用在后台使用
ACCESS_FINE_LOCATION权限访问设备位置信息时,用户会看到后台位置信息访问权限提醒。 - 由联系人提供程序组件管理的联系人亲密程度相关数据的访问方式有所不同:应用无法向数据库中写入联系人亲密程度数据,也无法读取此类数据。这会影响与来电者相关的 API。
配置简化
Android 6.0 及更高版本中的权限配置已经过简化。
- 由
init启动的服务的 Ambient 权能可将服务配置的所有方面的信息保存在单个.rc文件中。在为并非由init所启动的服务设置权能时,请改为使用fs_config.c来配置文件系统权能。 - Android 7.x 及更低版本使用设备专属的
android_filesystem_config.h文件来指定文件系统权能和/或自定义设备制造商 AID,从而扩展了 Android ID (AID) 机制。Android 8.0 及更高版本支持采取一种新方法来扩展文件系统权能。 - Android 8.0 将 USB 命令的处理从设备专属的
init脚本(替代 HAL 层)移至了原生 USB 守护程序。在每部搭载 Android 8.0 及更高版本的设备上,必须实现 USB HAL 接口。
