This page describes how GKI is released, including weekly, quarterly, and out of band emergency releases. The goal of this document is to give OEMs a guideline on where to pick up the GKI as well as the process for out of band emergency fixes. OEMs can also use GKI development to learn more about how they can work with the Android Kernel team to optimize the GKI kernel for their products.
GKI release cadence
GKI is released on a quarterly cadence post KMI freeze.
| Release Month | a12-5.10 | a13-5.10 | a13-5.15 | a14-5.15 | a14-6.1 | a15-6.6* | a16-6.12* | a17-6.18* | |
|---|---|---|---|---|---|---|---|---|---|
| October 2025 |
Check-in cut off GKI preload ready |
Oct 16 Oct 31 |
Oct 1 Oct 15 |
Oct 1 Oct 15 |
|||||
| December 2025 |
Check-in cut off GKI preload ready |
Dec 1 Dec 15 |
Dec 1 Dec 15 |
Dec 1 Dec 15 |
Dec 1 Dec 15 |
||||
| January 2026 |
Check-in cut off GKI preload ready |
Jan 16 Jan 31 |
Jan 2 Jan 15 |
Jan 2 Jan 15 |
February 2026 |
Check-in cut off GKI preload ready |
|||
| March 2026 |
Check-in cut off GKI preload ready |
Mar 1 Mar 15 |
Mar 1 Mar 15 |
Mar 15 Mar 31 |
|||||
| April 2026 |
Check-in cut off GKI preload ready |
Apr 16 Apr 30 |
Apr 1 Apr 15 |
Apr 1 Apr 15 |
May 2026 |
Check-in cut off GKI preload ready |
|||
| June 2026 |
Check-in cut off GKI preload ready |
Jun 1 Jun 15 |
Jun 1 Jun 15 |
Jun 15 Jun 30 |
Jun 15 Jun 30 |
||||
| July 2026 |
Check-in cut off GKI preload ready |
Jul 16 Jul 31 |
Jul 1 Jul 15 |
Jul 1 Jul 15 |
August 2026 |
Check-in cut off GKI preload ready |
|||
| September 2026 |
Check-in cut off GKI preload ready |
Sep 1 Sep 15 |
Sep 1 Sep 15 |
Sep 16 Sep 30 |
Sep 16 Sep 30 |
||||
| October 2026 |
Check-in cut off GKI preload ready |
Oct 16 Oct 31 |
Oct 1 Oct 15 |
Oct 1 Oct 15 |
November 2026 |
Check-in cut off GKI preload ready |
|||
| December 2026 |
Check-in cut off GKI preload ready |
Dec 1 Dec 15 |
Dec 1 Dec 15 |
Dec 1 Dec 15 |
Dec 1 Dec 15 |
||||
GKI build validity for OEMs
OEMs can use a recently released Android GKI. OEMs can launch with GKI-certified builds as long as they are compliant with LTS requirements in the Android Security Bulletin (ASB).
Quarterly certified releases
GKI quarterly releases contain a tested boot.img that includes a Google
inserted certificate to attest that the binaries were built from a known source
code baseline.
Each quarter, a GKI quarterly release candidate (not certified) is selected after the check-in cut off date, which is usually the second weekly build of that month. After the quarterly release candidate is selected, new changes won't be accepted into that month's release. During the closed window period, only fixes for bugs that cause test failure can be addressed. The release candidate undergoes quality assurance—as described in the GKI qualification section—to ensure compliance tests pass on GSI+GKI build with a reference device as well as cuttlefish.
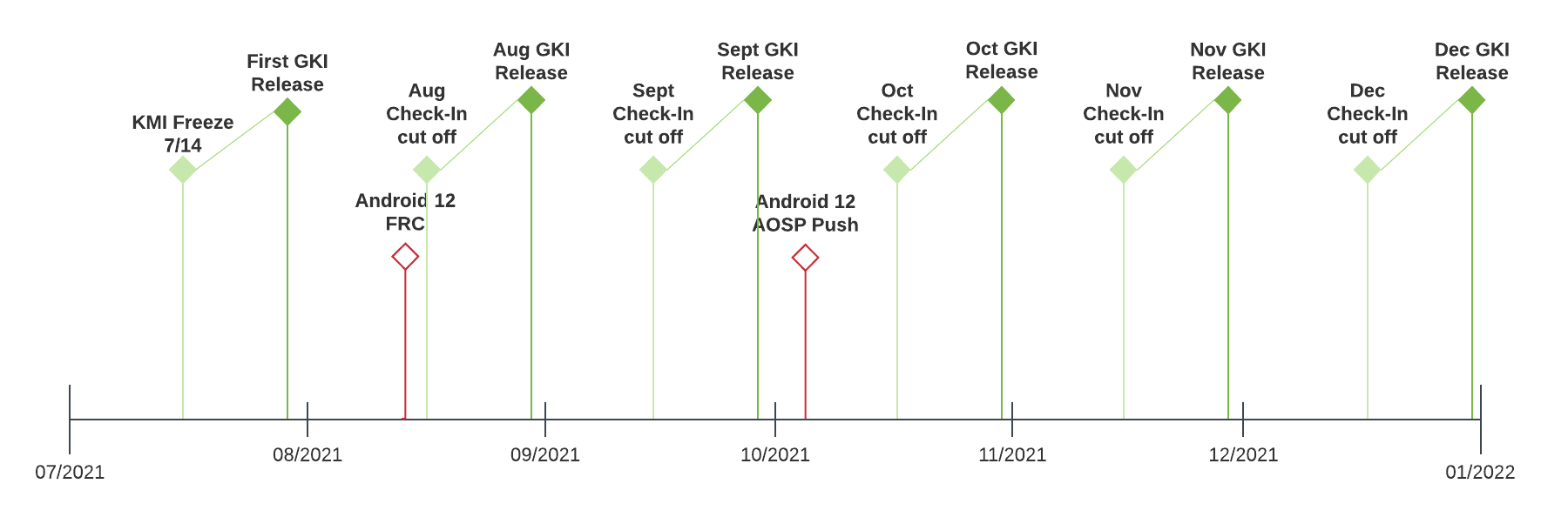 Figure 1. GKI release timeline
Figure 1. GKI release timeline
GKI qualifications
| Types of GKI builds | Quality enforcement | Notes |
|---|---|---|
| Weekly | Cuttlefish testing
|
|
| Quarterly (certified) | Cuttlefish testing
|
|
| Respins (certified) | Cuttlefish testing
|
|
Where to obtain build artifacts
Artifacts for all the releases can be obtained from ci.android.com.
You can find more information on the CI, including the test results on the Android Continuous Integration dashboard.
FAQs
Here are some frequently asked questions related to the GKI release process.
Is it possible to build a new GKI binary based on an already released GKI?
Yes, this is known as a respin. The respin process is supported as long as the released GKI build (on which the respin is requested) is compliant with LTS requirements in the Android Security Bulletin (ASB).
Is it possible to reproduce GKI binaries?
Yes, here's an example:
GKI 2.0
5.10 kernel prebuilts from build 7364300
https://ci.android.com/builds/submitted/7364300/kernel_aarch64/latest
To reproduce the example, download manifest_$id.xml and execute the following
command:
repo init -u https://android.googlesource.com/kernel/manifestmv manifest_7364300.xml .repo/manifestsrepo init -m manifest_7364300.xml --depth=1repo sync # build the GKI images # You may want to use LTO=thin to build faster for developmentBUILD_CONFIG=common/build.config.gki.aarch64 build/build.sh # (optional) build virtual platform modulesBUILD_CONFIG=common-modules/virtual-device/build.config.virtual_device.aarch64 build/build.sh
You can retrieve your GKI artifact copy from out/.../dist.
Has the GKI binary (including the emergency spin patch) been built on the latest codebase?
No. Respins only contain patches that are on top of the quarterly certified kernels that have been chosen. These respins contain all launch blocking bug fixes reported until any given time by OEMs using the corresponding base quarterly release. See the following example of how this type of scenario happens.
- OEM1 and OEM2 decide to use the GKI binary release from November 2021.
- OEM1 and OEM2 find issues that require patches for support. These patches may be different or may be the same.
- The respins over top of the November 2021 binary have launch blocking fixes reported by both OEM1 and OEM2 during the respin window, but nothing more.
- The issues mentioned in the second bullet are also included in subsequent GKI quarterly releases.
The October respin has all OEM submitted patches, but other OEM patches affect us, because they haven't been specifically tested with our products. Is it possible to only include our patch?
This isn't possible. A "per-OEM" respin path isn't scalable. Instead, the GKI team scrutinizes every single change that goes into respin builds, and tests the changes with all available hardware before creating a new build. If the GKI team finds that the issue is specific to an OEM, device, or model, the GKI team can ensure that the code added by the change only executes on the device, model, or SKU being affected.
The major benefit from unified respins is that every device that's using the same release base benefits from one another, especially if the bugs they discover are generic and applicable to all users. Core kernel bugs found in carrier testing is a specific example of this concept.
Are there situations where Google provides specific information about OEM patches and issue scenarios, so that OEMs can evaluate the impact and risk of implementing the patches with their products?
Google won't ever add a change to a respin build until the problem is understood and all of the details have been collected. This is seen in the changelog (commit message). Google does not reveal what specific device it affects, but OEMs can always find the issue description and solution in the changelog.
